Site Vulnerability Analysis and Counter-Terrorism
In an environment of growing concern about the prospect of acts of terrorism on American soil,
industries are establishing measures for assessing and managing site security risk. Some of these
industries are already subject to security-related regulation in response to the Public Health Security
and Bioterrorism Preparedness and Response Act of 2002 (Public Law 107-188), requiring them to
conduct systematic vulnerability assessments and implement risk-reduction and preparedness measures
as appropriate. Additional laws are under consideration currently by congress.
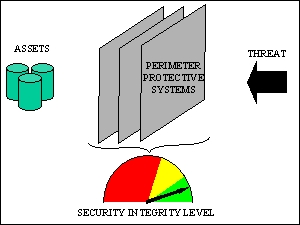
Among the requirements of these current and prospective laws is the performance of site vulnerability
studies to assess the risks associated with the potential for acts of terrorism. For industries handling
highly hazardous chemicals, the principal risks of concern are associated with the potential for acts that
could result in a major release of toxic, flammable or explosive materials from the site, or with the
potential for the theft of materials that could be used as precursor chemicals.
Various methodologies for systematic vulnerability analysis have been developed by industry groups
and government agencies. These include
| |
|---|
 |
a suite of risk assessment methodologies (the RAM methodologies) developed by
Sandia National Laboratories, sponsored by various government agencies, including the
EPA
|
 |
guidelines for analyzing and managing the security vulnerabilities of fixed chemical
facilities, sponsored by the AIChE Center for Chemical Process Safety, and
|
|
| |
|---|
 |
a guide to site security, developed by the American Chemistry Council
|
among others, such as the U.S. DHS.
The analysis of chemical security, like chemical safety, is based on systematic evaluation of
vulnerabilities at the site, and subsequent identification of reliable administrative and engineered means
of risk control. A vulnerability evaluation in the context of security risk typically involves several steps:
| |
|---|
 |
Identify critical assets
|
 |
Identify and assess potential threats
|
 |
Estimate potential consequence severity if an attack is successful
|
 |
Perform analysis of protection features
|
 |
Characterize the risk associated with each hypothetical scenario
|
 |
Identify and analyze risk-reduction options
|
 |
Select prevention/preparedness options and validate.
|
Often, advantage may be taken of certain safety/risk studies already in place for a chemical process.
For example, a process hazard analysis (PHA) can facilitate an understanding of the type of release that
could result from various hypothetical process boundary failures (release rate, chemical composition,
chemical phase, release duration, potential to mitigate, etc.).
Similarly, consequence analyses may provide an
indication of the potential degree of impact of a release, and of appropriate means of emergency
response. This type of information, as part of an integrated security assessment, can provide a strong
basis for pinpointing the principal site vulnerabilities, and assessing the efficacy of various risk-reduction
options.
The Unwin Company team represents substantial experience in the conduct of risk-based vulnerability and security studies,
including application to drinking water systems, dams, and nuclear facilities.
|